You’ve been busted!
Due to poorly developed plugins, Wordpress blogs are prone to hacking.
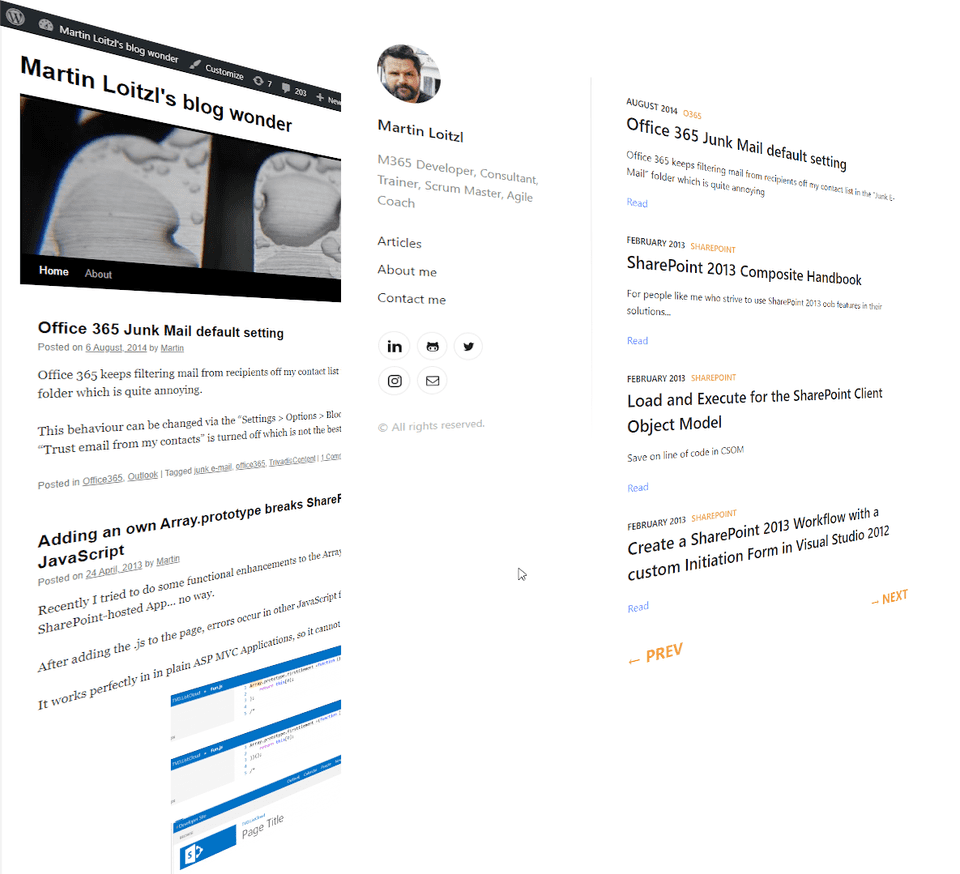
Luckily I wasn’t using any of those most dangerous Wordpress plugins mentioned in this article, but just like many others, my weblog got abused for cross-site-request-forgeries and phishing - using php files that have been uploaded years before through exploits.
At the end my account got locked and I lost interest a little.
But, I still had some old backups.
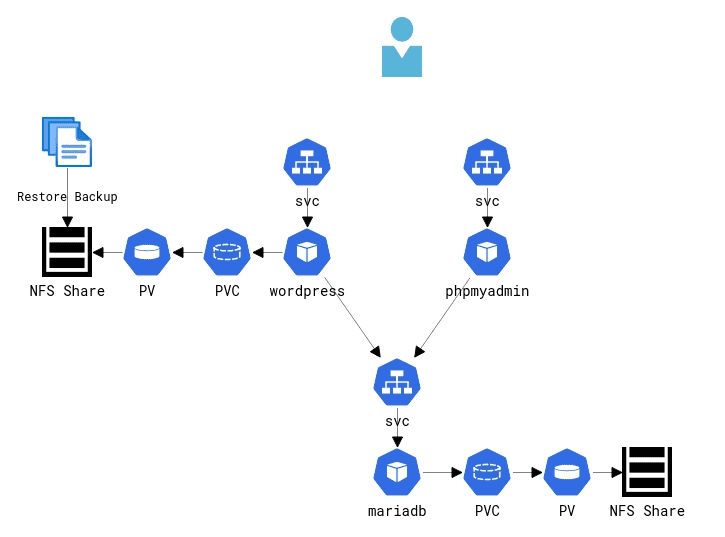
On my beloved homegrown k8s cluster I was able to fire up some old php containers, a new mariadb and phpmyadmin.
I restored the backup files into the persistent volume, imported the SQL dumps to mariadb, some more tweaks and we are ready to go.
$ kustomize edit set namespace old-blog
$ kustomize build | kubectl apply -f -
$ kubectl run -i --rm --image=arm64v8/mariadb:10.5 --restart=Never mariadb-client -- mysql -h mariadb -ppassword -e "create database wordpressdb"
$ kubectl run -i --rm --image=arm64v8/mariadb:10.5 --restart=Never mariadb-client -- mysql -h mariadb -ppassword wordpressdb < wordpressdb.sql
$ kubectl run -i --rm --image=arm64v8/mariadb:10.5 --restart=Never mariadb-client -- mysql -h mariadb -ppassword -e "create database gallery2db"
$ kubectl run -i --rm --image=arm64v8/mariadb:10.5 --restart=Never mariadb-client -- mysql -h mariadb -ppassword gallery2db < loitzlco-gallery2.sqlComes in quite quite handy for (manually) migrating and updating (dead links, etc.) to my new statically generated gatsby blog.